PART 1
This series of blog posts will outline the steps taken to stand up a cyber security lab using Microsoft's Hyper-V. This lab will be used for everything from
running Kali LINUX penetration testing tools, offensive countermeasures and techniques using tools like Active Defense
Harbinger Distribution, cyber forensics, and anything else that I may
choose. I will be using a hosted Hyper-visor for the lab, Microsoft's Client
Hyper-V running on Windows 10 Professional. Anyway, enough is enough let’s get started!
The first thing we have to do is to navigate to Control Panel -> All Control Panel Items -> Programs and Features.
The first thing we have to do is to navigate to Control Panel -> All Control Panel Items -> Programs and Features.
Next enable the Hyper-V option
The first server setting that we will configure is Virtual
Hard Disks (VHD). The VHD setting identifies where on our host system the vhd
(or vhdx) files will be stored.
After identifying where to store the vhd and vhx files we
will do the same for Virtual Machines. On the left pane select Virtual
Machines. This setting specifies the default folder to store vm configuration files.
Next is Physical GPUs. This setting determines whether or
not VMs with have direct hardware access to any installed GPUs on our host
system. This setting is not applicable to our environment so we will make sure
that Use this GPU with RemoteFX is unchecked.
We will also leave the next setting, NUMA Spanning and
Storage Migrations alone as it too is not applicable to our environment (if
you want to know more about this setting you can read about it at https://technet.microsoft.com/en-us/library/dn282282(v=ws.11).aspx).
We will also not be doing anything with the Storage Migrations setting as we
really don’t have a need to move or migrate any VMs in our lab environment.
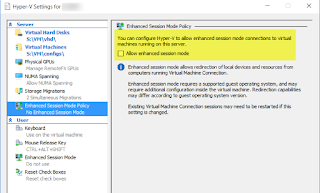
The final server setting, Enhanced Session Mode Policy, is
one of the most import. You can find out more about it HERE
but in a nutshell this setting provides
functionality similar to the way RDP allows access to local resources and Enhanced
Session Mode brings similar functionality using VMConnect. One
needs to be very careful with this feature because this is where one can break
segmentation and isolation between the VM host and the VMs in the lab setup.
And since we will be using this lab for all sorts of nefarious things as a
precaution we will NOT be enabling this feature. We can always enable it in the future should it be needed.
Finally, we have the User
Settings. These are pretty straight forward and do not require any
customizing. The only thing to check and verify is ensure that the Use enhanced session mode box is unchecked.
Once complete click APPLY and then OK








No comments:
Post a Comment